BASE DOCUMENTS
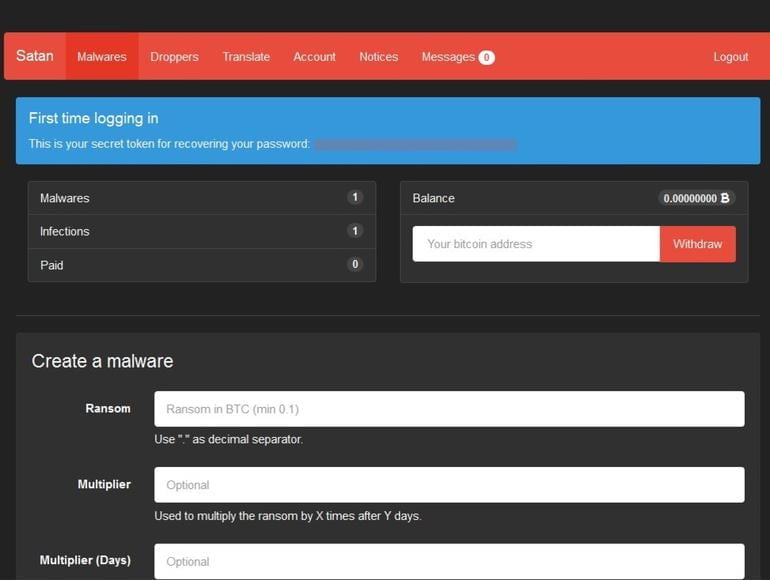
DailyPost 481 BASE DOCUMENTS Documents which provide the purpose, definition, ingredients & the modalities to create, operate & facilitate achieving the results can be termed as Base Documents. Though all of us are in search of such documents to gather basic functional knowledge of the topic, project or technology, it is goes unexpressed. The creation […]