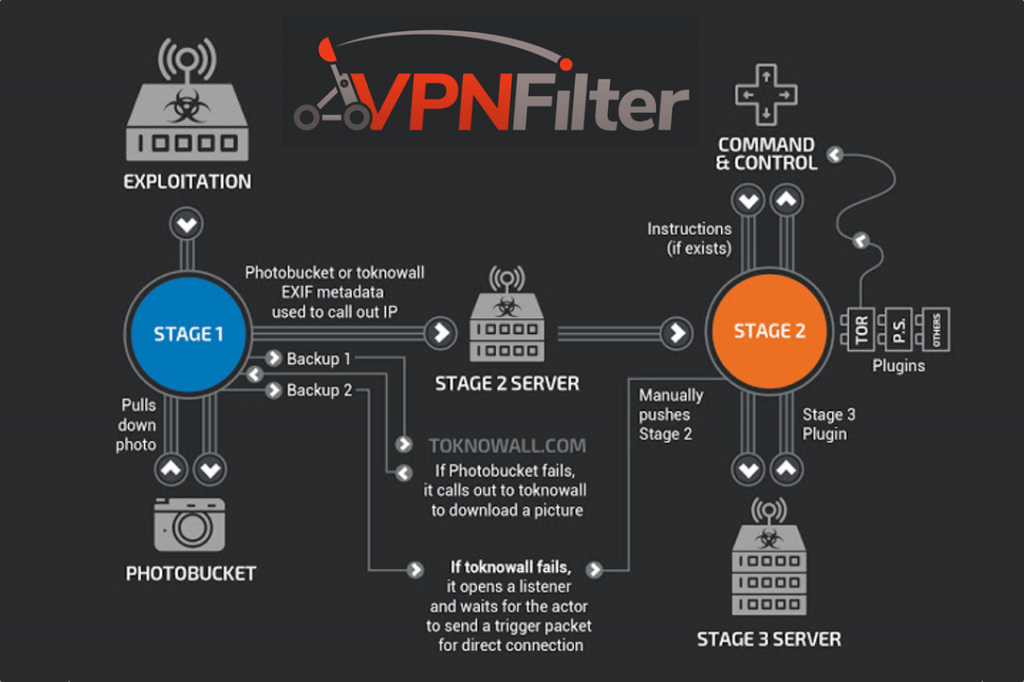
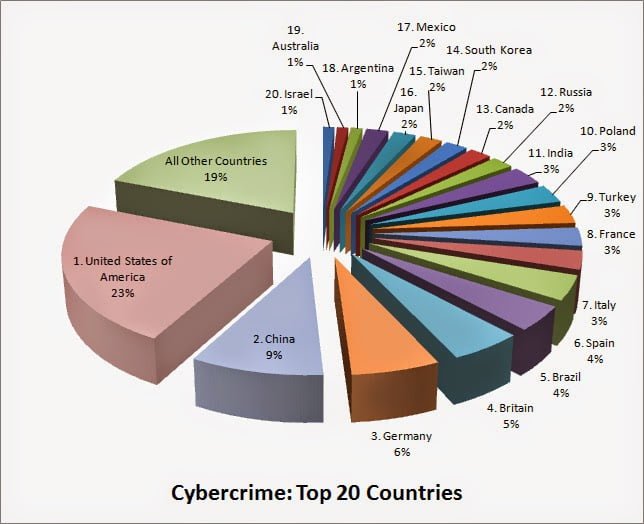
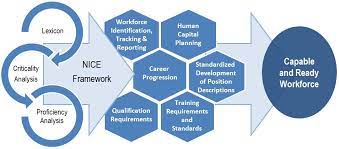
X-ROAD ESTONIA: THE DATA MAGIC
DailyPost 615 X-ROAD ESTONIA: THE DATA MAGIC Interoperability services is the future of data. Data is at the centre of governance. Citizen centred state & service oriented information system require to function as an integrated whole: one single operational information system. Ease of usage is the touchstone – data needs to be requested only once […]
X-ROAD ESTONIA: THE DATA MAGIC Read More »