DailyPost 2074
TOKENIZATION
When all critical assets and transactions of life become a bunch of numbers, which if falls into wrong hands, can wreak havoc on you, what does the system do? Can it rely on the integrity and goodness of people for running the system? The volume transactions are huge. Can the system wait for the hack to happen and then react? Will punishment and the consequent deterrence be able to run the system properly? All the above are non-workable solutions, however much we must try to make it happen. With all personally identifiable information inclusive of financial and likely transactional details having the potential to find its way into the public domain, without too much of an effort, for the wrongdoer, a new system needed to be devised for the purpose.
The system created to ward off this danger, and create a smooth and secure transactional tool and a mechanism based on it, is known as tokenization. ”Tokenization is the process of replacing sensitive data with unique identification symbols that retain the essential information about the data without compromising its security.” Data is the biggest asset today, and PII type data its primary concern. Cyber security at the individual level is completely dependent on it. Any dent in its failsafe environment can be suicidal to financial transactions and hence hazardous for the economy. Tokenization by its very nature, undertakes to minimize the amount of data a business needs to keep at hand.
With digital financial transactions taking the center stage for a variety of reasons, it has become a popular way for small and midsize businesses to bolster the security of credit card and e-commerce transactions. On the other hand, it solves a huge compliance issue as well. Tokenization minimizes the cost and complexity of compliance with the industry standards and the prevailing government regulations. Who all can benefit out of it? In theory, this technology can be used with sensitive data of all kinds. The expanse can be huge; from bank transactions, medical records, to stock trading and voter registration. ”Any system; a surrogate may use as a stand-in for sensitive information can benefit from tokenization.”
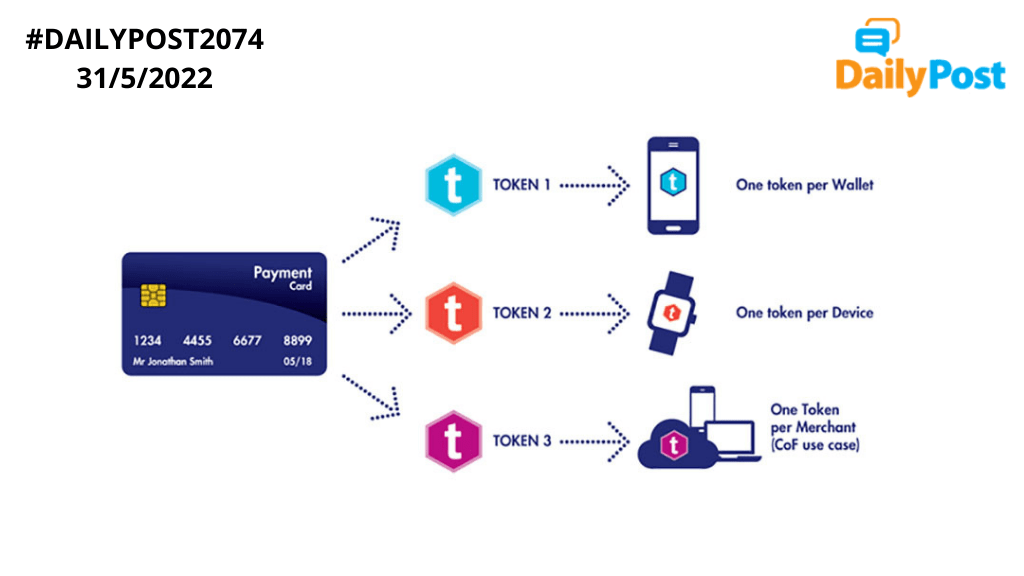
A payment processor often protects credit card data, bank account information and other sensitive information handled by it by tokenization, would have been made clear by the process explained earlier. Tokenizing sensitive credit card data include mobile wallets, e-commerce sites, and businesses that keep a customer’s card on file. ”Tokenization in the process of substituting sensitive information with equivalent non-sensitive information.” The non-sensitive, replacement information is called a token. Token can be created in different ways; by mathematically reversible cryptographic function, using non-reversible function or using an index function or randomly generated number. Tokens are all pervasive today and given the pace, volume and complexity of our transactions, tokenization provides a cyber secure environment, which its existence necessitates. Blockchain is taking it to the next level.
TOKENIZATION IS THE SECURITY MARVEL OF OUR DIGITAL TRANSACTIONS.
Sanjay Sahay