DailyPost 621
PROWLI MALWARE OPERATION
While we fathom out nature and dimensions of one hack, newer ones pose challenges, way beyond the past one. The hackers passion for research & deliver from their point of view is making the cyber world a veritable mine field. Cyber researchers are doing yeomen service to discover dark alleys of cyber world. The latest one is Prowli & is discovered by the GuardiCore Security team.
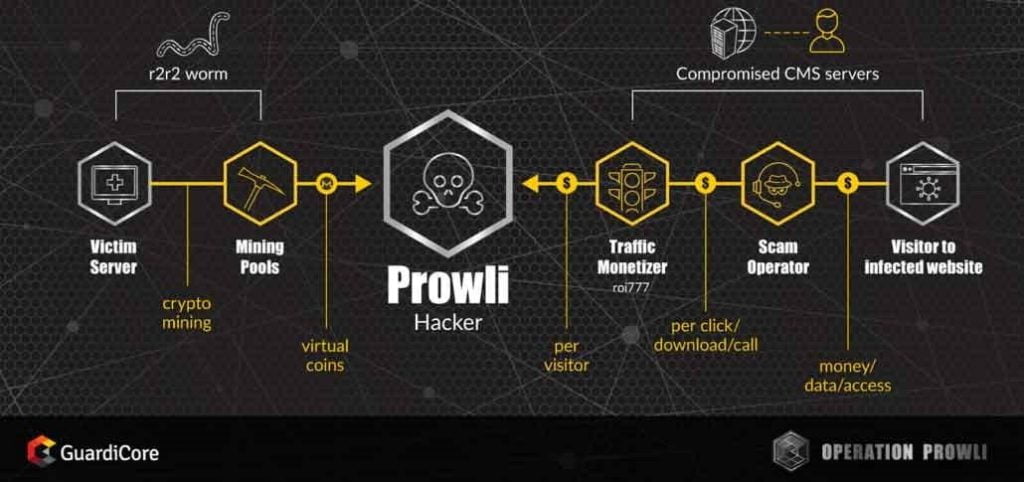
Through this operation the cyber criminals have successfully assembled a gigantic botnet of over 40,000 infected web servers, modems & IoT devices and used it for crypto currency mining & for redirecting unsuspecting users to malicious sites. A diverse botnet operation relying on vulnerabilities & credentials brute force attacks to infect the devices & take over. These types of crypto-jacking attacks are escalating.
Over 9000 companies have already been victimised. Prowli was first identified on 4th of April, 2018, when a group of secure-shell (SSH) attacks were found to be communicating with command- and- control (C&C) server. Attackers were behaving in a similar manner, having a communication with the same C&C server. The purpose was to download a number of attack tools named r2r2 along with a crypto currency miner. Hacking for crypto currency mining. This is a financially motivated indiscriminate attack going against domains exposing wide range of services to the internet. Prowli exploits known vulnerabilities across WordPress, Joomla!, SMB & even some DSL modems. The attackers even take over accounts in large-scale public computing environments
As known vulnerabilities are exploited, so automated patching ought to happen with continuous assessment & remediation. The network traffic has to be vigorously examined, which would help users to discover if they are infected. Segmentation is a good practice. ”Monitoring connections would easily show compromised devices communicating with crypto currency mining pools.”
CRYPTO-JACKING ATTACKS ARE THE NEW RANSOMWARE.
Sanjay Sahay